Our Post-Privacy World
Total information awareness may make us feel safe, but will we regret living in a surveillance state?

In 1786, Jeremy Bentham was visiting his younger brother, Samuel, an engineer overseeing the laborers on one of Prince Potemkin’s Russian estates, when he learned about his brother’s invention of the panopticon. Samuel’s idea was to create a circular structure incorporating the “inspection principle.” This would allow a limited number of overseers to extract the maximum amount of labor from workers. Watched from a central vantage point, and not able to see into the tower looming over them, workers, fearfully exposed and constantly visible, would end up surveilling themselves.
Bentham, the great utilitarian tinkerer, took his brother’s idea back to England and tried to interest the government in building panopticon prisons. Forced laborers outfitted with looms and controlled by the inspection principle could become a profit center for the state. Bentham died before his vision was realized, but the panopticon as an “institution of discipline,” as French philosopher Michel Foucault called it, has become a model for the working world at large. Bentham foresaw that his architectural designs could be used for factories, asylums, hospitals, and schools, and by the time George Orwell was writing 1984, Big Brother had moved from a tower into a TV screen that watched people around the clock.
Surveillance systems used for the management and control of people rank among the most important technologies developed over the past 200 years. They rely on networks of agents, whether human or artificial, who are trained or designed to analyze the deluge of data produced by surveillance. The first step in developing this technology was the making of lenses for enhancing the power of the eye. Affixed to a camera, lenses, along with sensors, actuators (components that control a mechanism’s function), and other autonomous agents, now scrutinize our bodies, both inside and out. The desired end to this surveillance is total information awareness. At first, we resisted this project, but in the era of pandemics, environmental war, and randomized terror, we are learning to embrace surveillance as a new form of social media. We are building networks that address today’s anxieties while ignoring tomorrow’s regrets.
Lenses ground from quartz were manufactured in Egypt 5,000 years ago, and optical lenses made from rock crystal were produced in Mesopotamia 3,000 years ago. Eyeglasses first appeared in northern Italy in the late 13th century, and by the early 1600s, the Dutch were applying for patents on spyglasses. After Vermeer used a camera obscura to paint his domestic scenes, Joseph Nicéphore Niépce invented the world’s first functional camera and in 1827 shot a picture outside his window in Burgundy. Relatively quickly, cameras became so common that hobbyists were using them to compile photo albums and to film home movies. The fisheye lens was invented in 1905, and the first zoom cinema lens was patented in 1927. The next major breakthrough was the invention of nonglass lenses. The Perspex lens arrived in 1934. Plexiglass hit the market a year later. Soon DuPont and Dow Chemical were making their own cameras with lenses molded from acrylic, Lucite, and other thermoplastics.
By the latter half of the 20th century, injection-molded plastic camera lenses cost pennies a piece. Photographic film was replaced by digital storage and the development of sensors capable of transforming fuzzy images into sharp likenesses. Then in rapid succession came advances in artificial intelligence, facial recognition, closed-circuit television, motion detectors, GPS, night vision, and other network-enabled technologies for tracking, scanning, and recording human behavior. The panopticon had become a fully automated surveillance system and helped to define the modern world in which we live.
By the end of the next decade, we might well have a trillion sensors operating on the surface of Earth. Our smartphones, augmented reality glasses, robots, medical wearables, and “smart dust” embedded with computers will total 50 billion connected devices—most of them talking not to us but to each other. This “Internet of things,” developed out of M2M applications (machine-to-machine systems), will control everything from transportation and logistics to home appliances and health care. Microelectromechanical systems (MEMS) are being shrunk to the level of nanoelectromechanical systems (NEMS). A nanometer is one billionth of a meter, which is roughly 100,000 times smaller than the diameter of a human hair. If MEMS are good for building video game controllers and gyroscopes, NEMS are good for building pumps and motors, and not just any pumps and motors, but devices small enough to operate inside our bodies. While measuring white blood cell counts, electrolytes, menstrual cycles, and other bodily functions, our smartphones will be live streaming our daily existence.
One of the first and largest sensor networks was designed by former auto executive and then Secretary of Defense Robert McNamara. During the Vietnam war, McNamara wanted an automated system for “sniffing” the presence of human beings or “hearing” them move supplies down the Ho Chi Minh Trail. Employing remote chemical, acoustic, and seismic sensors draped from trees or disguised as plants or bugs, some of McNamara’s “people sniffers” detected sound or motion, while others were sensitive to metal objects or human sweat and urine. Radio signals from these sensors were relayed to a computer-laden Infiltration Surveillance Center at Nakhon Phanom Air Base in Thailand. From 1968 to 1973, the surveillance center, then the largest building in Southeast Asia, housed the United States’ multibillion-dollar effort to build an electronic battlefield. While McNamara was embedding sensors along the Ho Chi Minh Trail, the North Vietnamese were foiling his investment by hanging buckets of urine from trees or sending water buffalo down the trail in advance of their troops.
The electronic battlefield later moved to Afghanistan and Iraq and the five other countries where the United States is currently at war. It was also repurposed for civilian applications. The “wall” now being built along the Mexico border is primarily a virtual barrier—a network of sensors, actuators, drones, and surveillance cameras that scramble Customs and Border Protection agents in Ford Raptors. This technology is now moving into our “smart” homes.
The term Internet of things was coined in 1999 by Kevin Ashton, an assistant brand manager at Procter & Gamble. Ashton wanted to use radio frequency identification (rfid) to check the stock in P&G warehouses. rfid tags could track widgets or humans or whatever else one wanted to follow. Rather than counting every object, it would be much simpler to develop an algorithm directing the objects to count themselves. As the industrial Internet goes operational, Google is selling thousands of doorbells that double as networked surveillance cameras, connected to either your home computer or the police, and Google’s Nest brand is selling more than 100,000 “smart” thermostats a month.
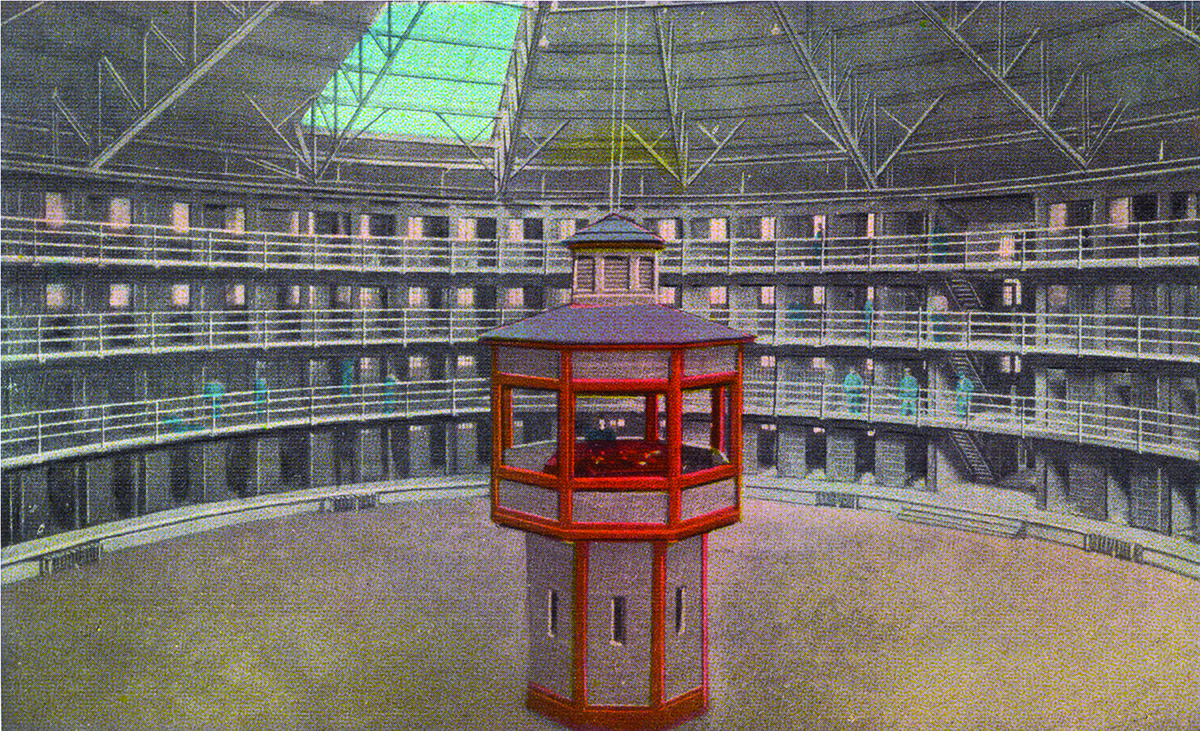
Panopticon prisons, like the Illinois State Penitentiary, afforded guards an uninterrupted view of every prisoner’s cell. (Chronicle/Alamy)
Today, China leads all other nations in collecting data on its citizens and controlling them through surveillance. Nine of the 10 most surveilled cities are in China, whose Sharp Eyes program has installed close to 200 cameras per thousand citizens in Chongqing, with a population of more than 8.5 million, leaving virtually no public space free of scrutiny. Soon, according to reports on “brain surveillance” in the South China Morning Post, it will move from external surveillance to personalized surveillance and internal surveillance, in which the state literally gets into your mind and under your skin. China used Western technology to build this network and is still aided by companies such as McKinsey, Hewlett Packard Enterprise, and Intel, but China now has its own multibillion-dollar surveillance industry and is exporting its facial recognition technology and “smart city” AI surveillance systems to 63 countries around the world.
After banning Google, Facebook, Twitter, and most Western news sources, China created a parallel universe of Internet services and media sites firmly under its control. It accomplished this using a Red Army of censors along with two million trolls, nicknamed the Fifty Cent Party because they were rumored to earn 50 Chinese cents for every fake social media message they posted. Harvard University professor Gary King, together with colleagues Jennifer Pan and Margaret E. Roberts, experimented by setting up a social media site in China and tweaking the content to see what got censored—either removed completely or flooded with comments from people parroting the party line, a process that King calls “strategic distraction.” He estimated that 450 million social media comments per year were generated by trolls paid by the government. Today, troll armies and bots devoted to strategic distraction are flooding the web around the world, and Western governments are not shy about wanting to emulate Chinese levels of surveillance. In 2020, reporters from The Washington Post and two German news agencies revealed that the leading company for helping governments encrypt their communications, a Swiss outfit called Crypto AG, was actually owned by the CIA.
In May 2019, San Francisco became the first major U.S. city to ban facial recognition, asserting that it was rejecting “Big Brother technology.” Somerville, Massachusetts, and other cities followed suit, but what looks like a noble act of resistance may prove to be little more than a symbolic gesture. After all, most of us embrace the same spooky technology used for policing public spaces when it organizes our photos, locates friends on Facebook, and logs us into our computers. San Franciscans are already digitized, tracked, profiled, and otherwise inscribed into the vast network of credit scores, game playing, policing, censoring, and commerce that make up the panopticon of modern life. Michal Kosinski, a computational psychologist at Stanford University’s graduate school of business who “studies people through the lenses of big data and the digital footprints we leave behind,” estimates that a yearly average of 62 gigabytes of data is generated for each person in the world. Yet Kosinski believes that it takes only 10 “likes” for Facebook to know us better than our work colleagues, 150 to know us better than our friends and family, and 300 to anticipate our behavior better than our spouse. Compounded with information from Amazon, Google, and elsewhere on the Internet, millions of data points swarm around each one of us. During the ongoing Covid-19 pandemic, as we abandon cities and face-to-face encounters and move toward digital marketplaces, “there is going to be no privacy,” Kosinski says. “We are already living in the post-privacy world.”
In 2002, the United States began a mass detection program based on the concept of predictive policing. Called Total Information Awareness (TIA), it was the “biggest surveillance program in the history of the United States,” said Senator Ron Wyden (D-Oregon), whose Senate Select Committee on Intelligence had nominal oversight. Although TIA surveillance supposedly ended in 2003, after predictive policing had been discredited as little more than racial profiling, The New York Times reported in 2012 that a variant of the program was still “quietly thriving” at the National Security Agency.
Proposed in 2002, shortly after the 9/11 terrorist attacks, TIA was the brainchild of Rear Admiral John Poindexter, a former national security adviser to Ronald Reagan and a major player in the Iran-Contra scandal. Poindexter had been banished to a K Street consultancy until he managed to get back into the Pentagon as director of the newly created Information Awareness Office. From there, he launched a raft of surveillance programs and set about developing online futures markets that could be used to predict terrorist attacks by monitoring betting pools on future events. This “terrorism futures market,” along with the divine overreach of his ambitions, forced Poindexter’s resignation in 2003. But we know from Edward Snowden’s revelations that mass surveillance continued unabated.
The Information Surveillance Center along the Ho Chi Minh Trail has been resurrected as the Utah Data Center built along the Mormon Trail in Bluffdale, Utah. This is where the NSA, in a $2 billion facility opened in 2019, is gathering the data used by “people sniffers” to monitor everything from computer keystrokes to eyeball iris scans. A program called mystic records and archives phone calls around the world. prism collects Internet communications. stingray tracks text messages. As its computers scroll through yottabytes of data, the NSA is trying to interdict enemy forces moving along the world’s electronic trails. “The U.S. government,” Snowden warned, “in conspiracy with client states, chiefest among them [co-members of the Five Eyes alliance]—the United Kingdom, Canada, Australia, and New Zealand—have inflicted upon the world a system of secret, pervasive surveillance from which there is no refuge.”
Although Poindexter’s program got shut down, the idea of using futures markets to predict political events has since been implemented in the Iowa Electronic Markets, where one can bet on the outcome of elections, and in Augur, a decentralized market built on blockchain technology. Total information awareness has also been adopted as the business model for Silicon Valley, where Google, Facebook, and other companies gather every scrap of information they can find and sell it to advertisers, political parties, Vladimir Putin, Brexiteers, or anyone else who wants to buy it. We might be uncomfortable with the government’s vacuuming up our data, but we have grown to love the companies that give us Alexa voice-activated speakers, crowd-sourced radar detection, and prepopulated, buy-again form fields. Poindexter’s vacuum cleaner approach to signals intelligence and surveillance—a dubious enterprise because of its inability to distinguish signal from noise—has been repackaged as “big data,” which allows Silicon Valley to form a comprehensive picture of people and their behaviors. The admiral was a man ahead of his times. The information coursing through NSA computers is indeed quite valuable, but markets and merchants, not spooks in the Pentagon, proved most nimble in using it.
In 2018, a columnist for The Guardian asked Google to give him all the data it had collected on him. The company turned over 5.5 gigabytes of information—the equivalent of three million Word documents. When I repeated this experiment in March 2020, Google informed me that I was being “tracked across fifty-one products” and that I should be patient while my data were being assembled. “This process can take a long time (possibly hours or days) to complete,” the company wrote. “You’ll receive an email when your export is done.”
Ten hours later, Google emailed to say that my “archive” was complete. When I unzipped the files, they contained 214.47 gigabytes of data, roughly equal to streaming 214 hours of movies on Netflix. As a book printed in 10-point Arial, it would be 13,893,796 pages long. The archive included all my contacts, photos, search history, purchases, call logs, and correspondence—pretty much everything I had done on the Internet from its origins to the present. Like everyone else, I had agreed to this surveillance by clicking “yes” to unread agreements that promised to “enhance your user experience.” Apart from Google, I am being tracked by a host of other companies. They scrape data from my financial transactions and then sell it back to me as my credit rating or pass it on to Bluffdale, Utah, as part of the NSA’s effort to comprehend information in its totality.
The history of electronic surveillance in the United States begins in 1864, when a stockbroker named D. C. Williams was convicted of wiretapping corporate telegraph lines and selling the information to stock traders. During Prohibition, the constitutionality of wiretapping as a police tool was narrowly affirmed by the Supreme Court. Wiretapping was used by corporations to root out union activity and by wives trying to catch philandering husbands. Today, eavesdropping—generally done by machines but also on occasion by humans—is what powers the voice-activated objects in our everyday world.
“Gentlemen do not read each other’s mail,” Secretary of State Henry Stimson said in 1929 when he shut down the Black Chamber, an early forerunner to the NSA. For 10 years, the Black Chamber, also known as the Cipher Bureau, had been the United States’ first peacetime codes and cypher organization. Black chambers, or cabinets noirs, had existed ever since the 17th century, when Louis XIV established the post office and secretly began opening and reading letters, a practice formalized when Louis XV created the Cabinet du Secret des Postes. In response, some people began to encrypt postal letters, and even Stimson, once he had become secretary of war during World War II and discovered that the military was relying on decrypting enemy communications, got back into the business of reading gentlemen’s mail. Since then, code breaking and electronic surveillance have become permanent features of the modern world.
After World War II, beginning with the formation of today’s 17 U.S. intelligence agencies and then expanding dramatically after 9/11 to include 2,000 private companies employing close to 500,000 people with top-secret clearances, the security business became one of the most rapidly growing parts of the economy. Traditionally conducted through the gathering of human intelligence, signals intelligence, and intelligence gleaned from other cognitive disciplines—in other words, an enterprise requiring interpretation and judgment—our newly automated security and surveillance systems rely instead on artificial intelligence and C4 (command, control, communications, and computer) systems.
Although it was a tragedy for the United States, 9/11 was a gift for the security state. As journalists Dana Priest and William Arkin later wrote in The Washington Post, “A culture of fear had created a culture of spending to control it, which, in turn, had led to a belief that the government had to be able to stop every single plot before it took place, regardless of whether it involved one network of 20 terrorists or one single deranged person.” Priest and Arkin reported that the “security spending spree,” which “exceeded $2 trillion,” had created an intelligence-industrial complex so large that it constituted a fourth branch of government.
Today, including government employees and civilian contractors, a million and a half people—roughly the population of Philadelphia—hold top-secret security clearances. So many people are duplicating the work of so many others that the United States has 51 federal entities and military commands in 15 U.S. cities tracking the flow of money through terrorist networks. Analysts are publishing 50,000 intelligence reports each year, most of them going unread.
“The federal-state-corporate partnership has produced a vast domestic intelligence apparatus that collects, stores, and analyzes information about tens of thousands of U.S. citizens and residents, many of whom have not been accused of any wrongdoing,” Priest and Arkin wrote. Domestic counterterrorism, aided by federal grants, now uses expensive tools and equipment to fight ordinary crime, “from school vandalism to petty drug dealing.” Local law enforcement has done what other agencies and businesses did after 9/11: “They followed the money,” allowing police departments to fly surveillance drones over U.S. cities and put armored vehicles on city streets from Davis, California, to Washington, D.C.
How much does this top-secret world cost the United States? The country’s 17 intelligence agencies have a “black budget” reported to be $85 billion per year. Adding to this cost are other intelligence operations hidden in the Pentagon budget, and here the numbers become much larger, with sums running into the trillions of dollars, according to the Congressional Budget Office, the Project on Government Oversight, and the Pentagon’s own Defense Business Board, which found that cutting waste and redundancy would save $125 billion over five years.
Each component in the nation’s huge security apparatus pretends to unique expertise, to being more knowledgeable than the others, which results in compartmentalization and the canker of secrecy. Plans exist for locking down the United States in the case of a national emergency and putting the country under martial law to ensure continuity of government (COG). Yet, in April 2020, during the coronavirus crisis, Congress proved incapable of functioning without face-to-face meetings in Washington. America’s COG plans were drafted by “experts”—military personnel, red-alert gamers, contractors, consultants, and other people endowed with top-secret security clearances. Daniel Ellsberg, who leaked the Pentagon Papers, refers to such people as “morons.”
On Christmas Day in 1968, Ellsberg flew from Los Angeles to New York City and checked into the Hotel Pierre, where he would brief Henry Kissinger on strategies for ending the Vietnam war. An expert in game theory, Ellsberg was an analyst at the RAND Corporation, a think tank in Santa Monica, California. Kissinger was a Harvard professor of government and an adviser to the newly elected president, Richard Nixon. Kissinger had visited RAND on November 8, three days after the election. “Richard Nixon is not fit to be President,” he said, but by December, after being appointed Nixon’s special assistant for national security, Kissinger had changed his mind.
Ellsberg was initially reassured by Kissinger’s appointment. The former professor was milder than the Nixon war hawks, and no one yet suspected that he and Nixon would continue the Vietnam war for another seven years. Soon after assuming his new position, Kissinger asked RAND “for a study of Vietnam ‘options’ to prepare for his first National Security Council meeting in January,” Ellsberg wrote in Secrets: A Memoir of Vietnam and the Pentagon Papers (2002). Ellsberg was chosen to lead this study.
Ellsberg spent two days briefing Kissinger. At the end of their final meeting on December 27, Ellsberg had the temerity to offer his older but less experienced colleague some advice. “You’re about to receive a whole slew of special clearances, maybe fifteen or twenty of them, that are higher than top secret,” he said. Ellsberg held many of these clearances himself, and he described what happens after being admitted to this exclusive club.
“First, you’ll be exhilarated by some of this new information, and by having it all—so much! incredible!—suddenly available to you.” Next “you will feel like a fool,” Ellsberg said, for having dared to write about government policy without knowing this information. “Then, after you’ve started reading all this daily intelligence input and become used to using what amounts to whole libraries of hidden information, which is much more closely held than mere top secret data, you will forget there ever was a time when you didn’t have it, and you’ll always be aware of the fact that you have it now and most others don’t … and that all of those other people are fools.”
One might eventually realize that this secret information is limited and perhaps of no greater value than reading The New York Times, but “in the meantime it will have become very hard for you to learn from anybody who doesn’t have these clearances.” Ellsberg said. “The danger is, you’ll become something like a moron. You’ll become incapable of learning from most people in the world, no matter how much experience they may have in their particular areas that may be much greater than yours.”
Ellsberg wished that long ago someone had warned him about the perils of entering the secret world. “I ended by saying that I had long thought of this kind of secret information as something like the potion Circe gave to the wanderers and shipwrecked men who happened on her island, which turned them into swine,” he wrote. “They became incapable of human speech and couldn’t help one another find their way home.” When Ellsberg later reflected on this meeting, he felt that Kissinger had not understood a word he had said.
Panopticon surveillance long ago moved from discipline to entertainment, but its troubling origins are reemerging as electronic surveillance becomes a tool for responding to the coronavirus pandemic. In 1999, Johannes de Mol in the Netherlands invented Big Brother, the television series that locked “house guests” into a camera-saturated space until one of them, after eliminating his competitors, won a cash prize. The show was franchised in more than 50 countries. In 2006, CCTV cameras in London’s East End broadcast their surveillance footage live on TV, along with an invitation for citizens “to see what’s happening … and keep an eye out for crime.” By 2020, China’s Skynet, Sharp Eyes, and other surveillance systems had placed more than 350 million CCTV cameras across the country, including AI facial recognition technology that can scan the entire Chinese population in seconds. These systems, along with social media apps installed on people’s smartphones, are being used for medical surveillance and other forms of social control. Globally, the world will have more than one billion surveillance cameras installed by 2021, when both the United States and China are projected to have one surveillance camera for every four of their citizens.
French philosopher Michel Foucault, in the “Panopticism” chapter in his book Discipline and Punish (1975), describes the measures adopted against the flea-borne plague that devastated Europe every third year during the 17th century. These measures included “a prohibition to leave the town on pain of death, the killing of all stray animals; the division of the town into distinct quarters, each governed by an intendant. Each street is placed under the authority of a syndic, who keeps it under surveillance. … Each individual is fixed in his place. And, if he moves, he does so at the risk of his life, contagion or punishment. Inspection functions ceaselessly. The gaze is alert everywhere.”
On reading these words, I was reminded of the last chapter in 1984, when Winston Smith, after “confessing everything, implicating everybody,” and after having lost his sense of time and memory in the face of surveillance so total that it seems to know even his innermost thoughts, gazes up at the face on the TV screen in front of him and realizes that “the struggle was over … He loved Big Brother.”
The world has gone viral. Viruses attack our computer operating systems (hence the need for cybersecurity). They attack our bodies (hence the need for emergency preparedness). They attack our countries (hence the need for homeland security). We have been transformed from doubly wise humans (Homo sapiens sapiens) into hosts for unseen agents that can kill us. In the new age of coronaviruses—named for the spiky crown of protein that the virus uses to hijack our cells—many of our interactions are now mediated through lenses and sensors that were developed for surveillance but are now embraced for social distancing and safety. The eye of Horus, the eye in the sky, the eye of the state, the endoscopic eye, the eye in our computers, smartwatches, and cell phones—we want a thousand eyes watching over us at this perilous moment in history. But wind the clock forward, and we may regret how we inoculated ourselves against not only fear but freedom.

